The Australian Cyber Security Centre (ACSC) has warned that healthcare systems are at risk of cyberattacks during the COVID-19 pandemic and that greater protection from malicious actors that seek to disrupt essential services is needed.
According to an ACSC report, Advanced Persistent Threats (APTs) are targeting crucial Australian infrastructure. APTs are sophisticated and well-resourced malicious cyber organisations; the goal is to compromise national networks to gain economic, legal, health, defence or security information that they can use to their advantage.
According to the report, cybercriminals may use a range of different methods: while some use simple techniques like phishing others will use high-end hacking tools. Cybercriminals are also often very organised, well resourced and tailor their attacks to optimise their chances of success and to minimise detection.
“APT actors pose the most significant threat to Australia’s national security and economic prosperity,” the report said.
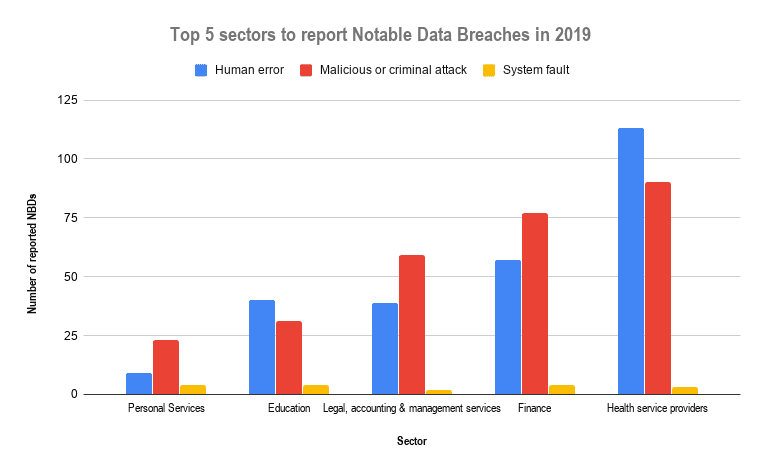
In a national report published by the Office of the Australian Information Commissioner, Australian health service providers were amongst the top five sectors to report significant data breaches in 2019.
The healthcare industry is a target for cybercriminals for several reasons, including their large databases of patients’ personally identifiable information, lack of sophisticated security measures and high numbers of endpoints and other devices connected to the network. The sensitive nature of patient data and makes it a prominent target for opportunistic criminals
Data and security breaches are extremely costly for healthcare organisations. According to the Ponemon Institute’s 2019 Cost of Data Breach Report, healthcare organisations across the world had the highest costs associated with data breaches for the ninth consecutive year.
Approximately $65.45 million dollars was lost globally, 65 per cent more than the global average of all industries.

Data source: Ponemon Institute’s 2019 Cost of Data Breach Report
According to Richard Buckland, Professor of Cyber-Crime, Cyber-war and Cyber-terror at the School of Computer Science and Engineering UNSW, “This decade has seen a shift as nation-states and funded organisations have started to dominate the world of cyberspace”.
Many advanced cyberattacks and data breaches have occurred in the past ten years. They have had wide-ranging impacts from revealing private user information en-masse to cutting off power grids in major capitals.
A recent example includes the 2017 WannaCry ransomware attack that targeted and disrupted 200,000 computers across 150 countries. The total damages ranged from hundreds of millions to billions of dollars. It disrupted and exploited data from crucial cyber networks, including that from hospitals. The solution is not so simple, according to Professor Buckland.
“The impact of WannaCry saw an increase in patient mortality, but there’s the interesting thing, it wasn’t due to WannaCry happening. After the hospitals were attacked they put in really strict security measures and that meant that people were slower to get to beds if there was a crisis, it was harder to get patient information and everything was a bit slower,” he said.
The report also stipulates a particular threat to the healthcare sector is transnational cybercrime syndicates that develop, share, sell and use sophisticated tools and strategies.
With a booming underground marketplace offering cyber-crime-as-a-service or access to advanced hacking tools, the probability of significant cyber-attacks has increased. The line between state-sponsored actors and cybercriminals are also blurring as the bar for entry is lower than ever.
In the report, the ACSC recommends health organisations implement a range of security controls to help mitigate the risk of being breached. As Professor Buckland notes, however, this is not something these organisations can do easily during a pandemic.
“We call pandemics low probability high impact events and an attack on the health system is probably viewed the same way. So how can you justify that in your budget?…the whole point of healthcare is that every spare cent they have is going towards looking after their patients,” he said.
As health organisations attempt to deal with the COVID-19 crisis and support their usual patients, there is a fear that implementing strict security measures will impede their ability to help their patients. As it did during the WannaCry attacks.
“Every second counts in hospitals, we can’t afford to be messing around trying to get access to patient information. People’s lives are on the line and as much we want to be secure, it, unfortunately, doesn’t really have top priority at the moment,” Canberra Hospital ED Doctor Chloe Jenkins said.
While this a noble sentiment, research indicates that a disruption caused by organised cyberattacks will have far-reaching effects which may include lack of access to critical clinical information and services, costly replacement of breached equipment, loss of community confidence and risks to patient safety and recovery.
So where does the responsibility lie?
“I don’t know if the responsibility should lay on hospitals, I think that this is a nation-level problem and requires a national-level solution… You wouldn’t expect hospitals to have their own army but when they invaded they need to be defended — but that’s usually something provided by the state,” Mr Buckland said.
This was echoed by Dr Jenkins who said: “I think it is important that the government dedicates some resources to healthcare’s cybersecurity because I worry that if we don’t start now, we are leaving ourselves wide open for an attack”.
The ACSC urges the health sector to implement Essential Eight threat mitigation strategies, with a focus on enabling multi-factor authentication, blocking macros and implementing data back-up plans.
One major recommendation, however, was to ensure all staff are educated in good cyber-safety protocols.
“APTs are also very patient adversaries, known to undertake detailed reconnaissance of high-value networks over months and sometimes years. They will also track representatives that work in the organisation they are targeting – in an effort to find the weakest link or point of vulnerability they can exploit,” it said.
As the world continues to shift towards a digitally-dominated environment, cybersecurity has become the next frontier.
“No one knows how to secure the cyber world … there is no perfect solution, but if we don’t start changing things now we will regret it,” Professor Buckland said.